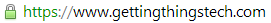We have not been affected by the Heartbleed vulnerability

In light of the news of widespread security vulnerabilities due to a poor implementation of HTTPS connections and SSL/TLS encryption, we want to ensure Getting Things Tech users that you are and have been safe browsing with us.
First of all, you probably don’t share a great deal of sensitive data with us. We don’t want it! From the start, we have been taking measures to keep your data off of our own servers, which are going to generally be more vulnerable simply because we do not have the resources to implement the best security features.
For instance, comments are through the common commenting platform Disqus. You sign in to comment with Disqus (or your social networking site that connects with Disqus), not Getting Things Tech. When you sign up to our mailing list, that information goes through our mailing list manager, MailChimp. We desperately want your donations, but we process them securely through PayPal or through BitPay if you want to use Bitcoins.
The idea is that we don’t want to be a potential point of failure for you on the web. Every place that you send sensitive information could forsake you, even if completely unintentionally. With that in mind, we try to keep away from all of the data we can.
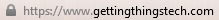
Nonetheless, we thought it was important to allow you to connect to Getting Things Tech via HTTPS. It is safer and keeps from anyone snooping on what you look at here, following what you click on, or grabbing secure data you might send to other websites from us. We put our money where our mouth is in that regard. You should always see something like these in your browser’s address bar when on Getting Things Tech, so that you are sure you’re browsing securely.
The Heartbleed vulnerability was related to servers, so we have looked into that situation. We are hosted on Dreamhost and do not use a version of OpenSSL that suffers from this vulnerability.
Since we are a WordPress blog, we sought to verify that WordPress’s backend wasn’t vulnerable. They don’t host anything for us, but you might be signed into WordPress when you visit here, meaning you could be unintentionally sharing data with somebody snooping on WordPress. This isn’t a realistic scenario, but nonetheless we are happy to say that we are running the new WordPress 3.8.2, which specifically took on the Heartbleed vulnerability.
If you have any questions or suggestions, please let us know in the comments. Otherwise, you can look for more information on the Heartbleed vulnerability on this page.
COMMENTS
Search
Related Posts
Recent Posts
- Make Prism.js show line numbers by default (without CSS classes)
- Hemingway App 3.0 update review: A gimmick becomes a real app
- Hugo vs. WordPress page load speed comparison: Hugo leaves WordPress in its dust
- Hemingway App 2.0 update: A worthwhile update comes with unfortunate price hike
- How to view academic journal articles off campus using your library's proxy
categories
Support This Site
Bitcoin Donations:18DP9TGdPN5usTKMRMfPk6Q2mSr4mAz8NJLitecoin Donations:
LPKQbDPykwjXr5NbXfVVQH9TqM5C497A16