Gmail will now encrypt your emails to protect you from NSA

According to the Official Gmail Blog, Google is taking new measures to protect your email data from snooping. They said that adding new security measures were “a top priority after last summer’s revelations,” referring to the widely reported NSA surveillance, which included intercepting emails sent via Gmail.
They are announcing two new measures. The first is that Gmail will always use an HTTPS connection when you are using it. HTTPS is far more secure than the older default HTTP connection, which left people open to spying, especially on public wi-fi. An HTTPS connection is fully encrypted, protecting all of your data from people who are neither you nor the recipient of the information (in this case, Google is the recipient).
Google has been implementing HTTPS for a while now, but starting today they have moved to implementing it fully; before, Gmail would sometimes use HTTP if their infrastructure was being stressed. However, in terms of NSA spying, the HTTP/HTTPS issue was not what led to emails being compromised.
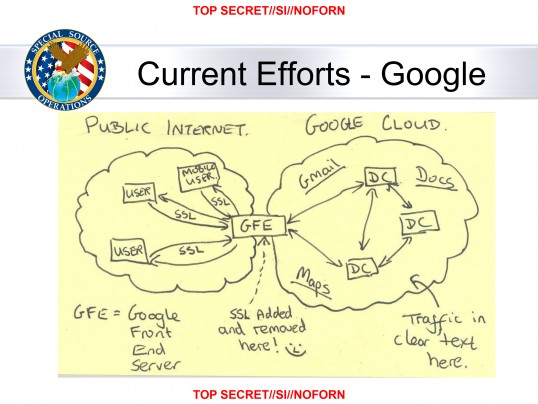
The NSA knew that Google was pretty reliable in terms of using HTTPS connections to protect communication on the internet, even before today’s full implementation. The vulnerability that the NSA exploited, at least according to Snowden-obtained documents, was the way Google moved data around internally. Google has various data centers and servers, since they serve so many users all around the world. Data moves a little bit like real mail, just nearly instantly. Google has a network of digital “post offices,” so to speak, which are connected by privately owned fiber optic and similar networking cables.
The public does not have access to the communications between Google data centers, so those data transfers were never encrypted. However, almost all the data Google receives is moved from data center to data center, meaning everything on Gmail was vulnerable at some point if those privately owned networks were compromised, which was something Google focused on protecting. The key vulnerability may have been when Google sent data from their internal data centers back to the public internet, according to information obtained by the Washington Post in October.
When Google sent information from a data center to you, it would add that layer of security before sending it to the public internet. This makes sense, since as we said the unencrypted (HTTP, basically) communications could be intercepted and read. Based on a diagram leaked from the NSA, it is suggested that the NSA had been able to intercept all the data at the moment right after data left Google’s data centers but before it was encrypted and went to the public internet. It may also be the case that the NSA had gained access to those private fiber optic cables by convincing internet service providers (such as Comcast, Time Warner, AT&T) to let them spy on the cable that Google rented from them, but the leaked information is inconclusive in that regard.
Either way, Google’s announcement today represents a tremendous step forward for protecting your data from outsiders, NSA or otherwise. While this is a close to foolproof means to protect you from a third-party grabbing your data in transit, that doesn’t mean your data is absolutely safe. You have to keep your end of the communication secure, meaning your passwords need to be secure. Likewise, Google still has broad rights to look at your emails, so you need to decide whether you want Google to have that information for whatever private uses they may come up with.
Yahoo was also implicated in the original NSA snooping story broken by the Washington Post. Their HTTPS implementation at that point was arguably far worse than Google’s and the NSA indeed seems to have collected more information from Yahoo users. CEO Marissa Mayer announced in November 2013 that by the end of Q1 2014, all Yahoo data center to data center communications would be encrypted by Yahoo and all users would have “an option to encrypt all data flow to/from Yahoo,” an odd opt-in implementation. They have not yet updated on whether these changes are complete.
Elsewhere, Facebook has also implemented this encryption on their data center communications. Twitter has a sterling reputation for security and resisting government intrusion into user data, but inexplicably cut off their plan to encrypt direct messages recently, though they have said they will be changing the entire way direct messaging works in the near future.
Featured image by BobMical (Flickr)
COMMENTS
Search
Related Posts
Recent Posts
- Make Prism.js show line numbers by default (without CSS classes)
- Hemingway App 3.0 update review: A gimmick becomes a real app
- Hugo vs. WordPress page load speed comparison: Hugo leaves WordPress in its dust
- Hemingway App 2.0 update: A worthwhile update comes with unfortunate price hike
- How to view academic journal articles off campus using your library's proxy
categories
Support This Site
Bitcoin Donations:18DP9TGdPN5usTKMRMfPk6Q2mSr4mAz8NJLitecoin Donations:
LPKQbDPykwjXr5NbXfVVQH9TqM5C497A16