Change your passwords at these sites in light of Heartbleed security hole
In case you hadn’t heard, a massive security flaw dubbed “Heartbleed” has affected around two thirds of web sites and was discovered by benevolent software developers on Tuesday. The net effect is that your passwords, and by association data, have been and are vulnerable. As more information is being gathered, we can help you figure out which accounts have been compromised.
While we suggest you check out our original story, the short version of things is that the software used to implement secure connections via HTTPS had a simple programming error that made it theoretically possible for hackers to get encryption keys (passwords) from “secure” web sites’ servers without leaving a trace. Since not a trace would be left and no widespread user account hijackings have occurred, nobody is too certain whether or how much this flaw had been exploited before its discovery.
However, making it public made all unpatched web sites extremely vulnerable. This was necessary to get people to fix the flaw, but in this short term window it has very openly jeopardized private information. Either way, this flaw has been around since 2011 and that means some of your passwords have been open season for hackers for years.
To put it briefly, you need to start changing your passwords as soon as possible. Before we move on with some of the web sites affected by Heartbleed, please bear two things in mind:
- If you use the same password at an affected website and an unaffected one, you need to change both. A clever hacker will have no problem realizing that “baseballguy2525” at Yahoo is also “baseballguy2525” at Google.
- To some extent, we have to trust each web site’s word on whether users have been vulnerable. We have been able to test for the past few days as to whether a site’s servers have this hole, but there is no telling if their servers were vulnerable over the past few years and have since been upgraded or changed.
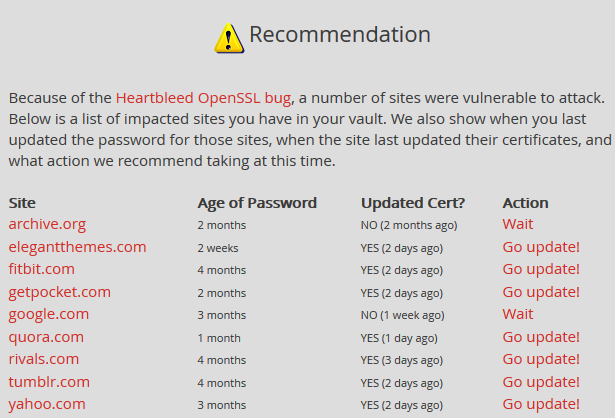
If you use LastPass, our favorite password manager, you can perform a “security check” from your vault and it will let you know which of your accounts have been affected as well as if you need to wait to change them. Why wait? If a website hasn’t patched things yet, you’ll just be exposing the new password to snoopers. This is very handy and will look something like this:
While LastPass’s servers themselves were vulnerable, their ingenious security scheme didn’t actually make anyone vulnerable because they deliberately set things up to be immune to these sorts of attacks in a variety of ways. Your data is all encrypted on your own computer before going to them and your passwords, the info that is most valuable to hackers taking advantage of Heartbleed, never goes to LastPass’s servers. It just isn’t there to steal. LastPass says you do not need to change your master password, because it is essentially impossible for the Heartbleed leak to have made it vulnerable.
Likewise, they use something called “perfect forward secrecy” which is an enhancement to HTTPS that makes it so that a leak like this doesn’t make every data transmission over the course of years vulnerable to becoming decrypted. Every unique communication between you and any website with perfect forward secrecy has a separate key used for decryption, making it necessary for a hacker to steal both the key and the browsing data at the same time.
Not a LastPass user?
First of all, we suggest becoming one! It makes keeping good password etiquette much easier and it will help you keep track of all the places you are made vulnerable when things like this happen. Check out our full write-up here. If you are a student, you can get their premium features free (normally $12/year).
Anyway, Mashable has been keeping a list of affected websites, too. A GitHubber automatically tested all 10,000 of the internet’s most popular websites to check their vulnerability moments after the leak was announced publicly, so you can consult that as well. We have looked for the most commonly used and problematic websites and have compiled them below for your convenience. Please let us know if there are any major places we have missed!
[vc_row][vc_column width=”1⁄1″][vc_tabs interval=”0″ style=”tab-style-three” title=”Heartbleed Affected Sites”][vc_tab title=”Social Media” tab_id=”1397160606-1-79″]
They are not sure if they were affected, but did at one point have servers running with this vulnerability. It has been patched and they suggest you change your password.
Same story as Facebook, their owner, except they didn’t patch the vulnerability until after the leak went public. Definitely change your password here.
Change your password, they were vulnerable and just recently fixed the problem. They don’t know of any accounts being hijacked just yet.
- Tumblr
As part of the Yahoo network, they have been vulnerable. Change your password immediately, things are now patched.
They’re saying that none of their servers are or were vulnerable, but they still did a security patch. That doesn’t make much sense. You may want to change your password, but it probably isn’t an urgent need.
- Google+
Google says that they are not currently vulnerable and are actively applying patches to their services. They have not commented on G+ specifically. Google told ABC that they do not see a need for users to change passwords, but you may want to just in case. An imgur user posted this screenshot of Gmail failing a vulnerability test, so Google may have sneakily fixed things across all their services. It isn’t clear, if this is true, why it would make sense to keep your old password. We haven’t been able to verify the validity of the screenshot.
- Gmail
Google says that they are not currently vulnerable and are actively applying patches to their services. They have not commented on Gmail specifically. Google told ABC that they do not see a need for users to change passwords, but you may want to just in case. An imgur user posted this screenshot of a testing website’s failed result for vulnerability. It has since been patched.
- Yahoo Mail
All Yahoo services have been hit. They quickly implemented the patch, but this should probably be your top priority for a password change.
- Mail.com
Mail.com appeared on this list of the top 10000 most visited websites on the internet that were automatically tested. It’s result? Fail. It has been fixed, so change your password now.
- Dropbox
They haven’t come outright and said it, but Dropbox did tweet that they had applied some patches. We’ll assume that they were vulnerable, then. Change your password.
- Box
Mashable reports an admission on the part of Box that they were vulnerable and have since applied the necessary fixes. Change your password.
- Google Drive
Google says that they are not currently vulnerable and are actively applying patches to their services. They have not commented on Drive specifically. Google told ABC that they do not see a need for users to change passwords, but you may want to just in case. An imgur user posted this screenshot of Gmail failing a vulnerability test, so Google may have sneakily fixed things across all their services. It isn’t clear, if this is true, why it would make sense to keep your old password. We haven’t been able to verify the validity of the screenshot.
- TurboTax
TurboTax said through a press release that they were in fact vulnerable from the Heartbleed leak and have implemented the appropriate fixes. Change your password and hope nothing too precious has already fallen into the wrong hands.
- USAA
They were compromised and have now finished implementing fixes, according to their blog. Change your password ASAP.
- GoDaddy
According to an official statement, GoDaddy’s servers were affected and they are in the process of upgrading. You need to change your passwords, but not until they are done.
- StackExchange
StackExchange failed this automated test done on the most popular 10000 websites just after the leak was announced. It has been fixed. Change your password.
- CreditKarma
CreditKarma failed this automated test done on the most popular 10000 websites just after the leak was announced. It has been fixed. Change your password.
- Wunderlist
The team posted immediately that they were vulnerable as well as their action plan for re-securing your data. All has been fixed. You’ll be signed out next time you use it, you’ll need to sign back in and change your password.
- Minecraft
The popular game was compromised, according to their blog. They suggest changing your passwords ASAP.
- Steam
The extremely popular platform for PC gaming was compromised. They have patched things up and don’t think any accounts were accessed. Valve suggests changing your password.
The following failed this automated test done on the most popular 10000 websites just after the leak was announced.
- XDA-Developers
- Archive.org
- OkCupid
- DuckDuckGo
- Squidoo
- 500px
- Weather.gov
- FatWallet
- ArsTechnica
- TheAtlantic
- Kaspersky
- Creative Commons
- Medium
And countless others. Look through it to make sure a site you use wasn’t vulnerable.
COMMENTS
Search
Related Posts
Recent Posts
- Make Prism.js show line numbers by default (without CSS classes)
- Hemingway App 3.0 update review: A gimmick becomes a real app
- Hugo vs. WordPress page load speed comparison: Hugo leaves WordPress in its dust
- Hemingway App 2.0 update: A worthwhile update comes with unfortunate price hike
- How to view academic journal articles off campus using your library's proxy
categories
Support This Site
Bitcoin Donations:18DP9TGdPN5usTKMRMfPk6Q2mSr4mAz8NJLitecoin Donations:
LPKQbDPykwjXr5NbXfVVQH9TqM5C497A16