Best web browsers for privacy and anonymity

Your web browser can open you up to all kinds of security risks, even as you change your browsing habits for the better. While some of the mainstream browsers can be configured to protect your privacy, some people either want something stronger or something simpler. With that in mind, we have your best web browsers for privacy and anonymity online.
You need to avoid tracking cookies
There are a few different ways your browser may be leaking your identity or otherwise exposing you to security risks. First of all, advertisers are constantly trying to slip you tracking cookies. What do these do? Well, when you visit a webpage with advertisements on it, you may also be automatically downloading a cookie (or cookies). Unbeknownst to you, this cookie will be relaying information about your browsing habits back to the advertiser in an effort to better target you with ads in the future.
While this might seem benign or not a big deal, it can be hard to foresee how this may affect you in the future. For one, there are simple problems like having the ads that are targeted to you reveal things about you. A simple example is this: you are shopping for a PS4 for your sibling and do some price comparisons, etc. Later, as you and your sibling are doing something completely different on the web, he or she notices that all the ads are for PS4s and accessories. The surprise is now ruined.
Unfortunately, that’s the least creepy and distressing of the possibilities. Sometimes, the entity tracking you is not as interested in targeting you for ads as they are _selling _this personal information. For now, pretty much the only people interested in buying this kind of information are other advertisers. However, it is a little discomforting to know that our browsing data and other personal info scraped from social media and the like are being bought and sold on an open, legal market.
Factor in security holes, too
Many browsers have garnered notoriety for being frequent victims of zero-day attacks. A zero-day attack is when an attacker, using some sort of malware, virus, or worm, finds the security vulnerability in a browser or other app before the creator of the browser or app finds it. It’s “zero-day” because that’s how long the developers of the vulnerable product have been working to fix it when the attackers hit. This is why Google offers million dollar bounties to people that find zero-day vulnerabilities; it gives good people motivation to find the holes before hackers do.
Zero-day exploits tend to be the kinds of problems that either plant invasive malware or viruses on your computer and/or steal personal information like your credit card or banking numbers.
One thing to note: part of the way zero-day vulnerabilities work is that you don’t find out about them until the bad guys do. It’s built into the definition. This means that finding more zero-day holes in one browser over another doesn’t necessarily make one more or less secure than another. It just means that hackers have more incentive to “break” the most popular browsers.
According to Secunia research, Opera is the browser which had the highest percentage of its users vulnerable to zero-day exploits in 2013. It is worth mentioning that Opera has essentially revamped their browser from the ground up since the beginning of 2013, so it is difficult to say whether that remains true. Firefox was the next most vulnerable by this margin, with a high amount of vulnerable users and a very high amount of vulnerabilities. Chrome had a lot of vulnerabilities, but not nearly as many affected users – this is probably because the browser updates automatically. Internet Explorer has a very, very poor reputation, but does well in terms of the total number of vulnerabilities.
It is just as likely that you become vulnerable due to plug-ins. Adobe Flash is famous for its poor security (and how bad the software is in general, which is why its being phased out by most developers). Flash accounted for the 5th most vulnerabilities among the 50 most used programs on Windows, according to Secunia.
Java ranks even worse and is even less necessary for the vast majority of web users, being the 3rd most exploited program. The key here is to reduce your points of vulnerability and both Java and Flash are little-used around the web nowadays and are famous now not just for the quantity of their security holes, but the severity of them.
Does your browser connect to HTTPS:// everywhere?
As we have discussed in other articles, the old standard web connection, HTTP, is not very secure. It is not difficult for hackers or surveillance agencies to look at all the data you exchange over an HTTP connection. What does this mean?
If you inputted your credit card info to a website that had HTTP:// to start its address, that information that you’re sending is potentially vulnerable. The HTTP refers to the format of the information you and the website are exchanging. HTTP is the old standard and is basically equivalent to passing a note in class; you have to hope that everyone who passes your note to the next person doesn’t open it up, because it won’t be hard to read it once they open it.
Sometimes, this isn’t a big deal. If you’re on Getting Things Tech, you’re not giving us secure information and therefore we do not even offer an HTTPS connection. HTTPS is the more secure protocol that websites are beginning to implement to protect you from snooping. As a matter of fact, the S actually stands for secure!
This works more like the drive-through at the bank. The back-and-forth between you and the website goes through its own fast lane that is only accessible to the people at each end. Any website that you are a member of or will be making purchases from, though, should offer this. Sometimes, they do, but your browser doesn’t bother connecting the HTTPS protocol. Better browsers will always connect to HTTPS when it’s available.
Is your browser collecting your data?
Under the guise of making your life more convenient, many browsers and services collect your data. This does, in fact, make things convenient. In Chrome, you will see your previous searches as you re-type them. This saves you a second as you can click instead of finishing that phrase.
Unfortunately, Google isn’t just providing this for the sake of your convenience. Think of all of this stuff going into an e-file that’s all about you. They get to know every single website you go to, every search you make, your favorite bookmarks, and more generally everything you do on the internet. It’s their business model. Collect your data, give you free services, sell your data to advertisers.
And, as we learned throughout the NSA scandal, it may also involve giving all of this information to the government if it asks, all without telling you or getting a warrant. While all of these companies are paying lip service to changing their ways, it seems inherently insecure to leave all of this personal information with any group, let alone ones that now have a reputation for sharing that info.
Head to page 2 for the best browsers for privacy and anonymity!
Our favorite web browsers for privacy and anonymity require no special tweaking or settings to make them safe for browsing on the web. There’s no such thing as absolute security or privacy, but we have several options to get you well on your way. We don’t like to pick an absolute favorite, because everyone has different needs. Check out each one and see which will work for you.
For privacy and ease of use: Epic Browser (PC/Mac)
We like Epic Browser because it is open-source, built on Chromium, and shouldn’t require you to learn much of anything to start browsing more securely.
Privacy-focused, Epic Browser doesn’t store your data, send your searches or URLs to Google or anyone else, rejects all cookies and trackers, disallows extensions, and offers a one-click proxy to shield your IP address. Since it’s built from the same basic code that Chrome is made from, it should feel easy to use, even for novice computer users.
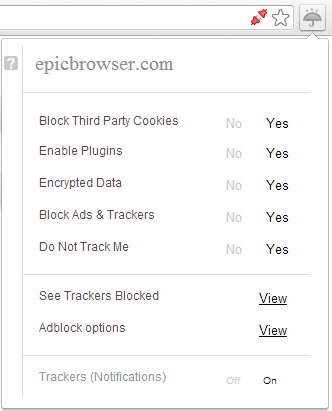
On your new tab page, Epic lets you know what it has been blocking. It blocked 69 trackers in just about 5 minutes of web surfing in our test. While it says it blocked 0 third-party cookies, it mentions in its information that its built-in AdBlocker blocks the vast majority of these cookies before the browser itself blocks them, resulting in a lower count.
The red graphic on the right of your omnibar (where you type URLs and search queries) is where you can click to turn on your proxy. When you click it to activate the proxy, it will turn green. The umbrella button brings up your privacy-related options.
Most of these are self-explanatory. Blocking third-party cookies, ads, and trackers are easy enough to understand. “Do Not Track Me” is a protocol being implemented across the web where browsers can notify third parties that are trying to send you trackers that you do not wish to be tracked. Some, but not all, honor this request. Epic blocks those who don’t. Encrypted data refers to preferring HTTPS over HTTP connections. “Enable plugins” is where you choose to turn Java/Flash on or off.
Pros: Near-perfect privacy settings out of the box, easy to use, open source, deletes all user data when browser is closed, no user data stored on the web
Cons: No extensions whatsoever, no Linux compatibility, proxy slows browsing down significantly
Download: Epic Browser website
For total anonymity, extensibility: Tor Browser Bundle
The Tor Project was initially designed by the U.S. government as a means for the military to securely communicate. Today, it has become popular for a variety of purposes both benign and of high importance. Where people must hide from government censorship or communicate with whistleblowers, they always choose Tor. This is not to say that Tor users are all into shady dealings; to the contrary, it only works because the network is filled with people who just want privacy and anonymity in their everyday web use.
Why is that? See, your typical web browsing involves data going from you to the website you’re visiting and vice versa. When you’re browsing with Tor, the data you send and access is routed through a series of “nodes,” which is a fancy word for designated computers on the Tor network. Some people elect to act as nodes (it is optional), and by the time all is said and done, it is impossible to tell which of the countless computers that were involved in sending this information was the originator.
If you were avoiding somebody who was following you on the road, you would try to take the most random route possible to your destination. This would make it difficult to tell where you were headed at any point in time as well as difficult to follow. With Tor, your data is re-encrypted between each node as well. Think of this as the equivalent of instantly switching into a new car at every turn. Nobody knows the full route – not the website you visit, not any trackers they try to send you, not any of the nodes you go through on the way, and not even you, because you don’t know which nodes you head through on the way, since their anonymity is protected too.
- Source: The Tor Project
- Source: The Tor Project
- Source: The Tor Project
While there is more than one way to use Tor, we’re going to focus on the Tor Browser Bundle, which is a browser that only uses the Tor network.
It is based on Mozilla Firefox ESR, which is the most stable and secure version of Firefox. It is modified from there, but only to make all of your traffic go through the Tor network as well as configuring the settings in the most privacy-friendly way. Like Epic, TBB doesn’t store your data in a server, send your searches to mainstream search engines that save your searches, or accept trackers and cookies.
An advantage over Epic Browser is that you can download any Firefox-compatible browser extension. However, this is risky business. Many extensions send your browsing data to a third party and some others, when poorly-coded, leave you vulnerable to other security threats. Nonetheless, having the option to install trusted extensions like our favorite password manager LastPass is a plus. It comes standard with extensions like HTTPS Everywhere that are open source and protect your privacy.
I would consider Tor Browser Bundle slightly less user-friendly than Epic Browser, but it is by no means something that requires a steep learning curve. At first glance, it is hardly distinguishable from Firefox. For most users, you don’t need to do much of anything differently to use it as you would Firefox or any other browser, either.
Pros: You will be very hard to identify online, it can have extensions, has a great privacy configuration, uses a familiar interface, compatible on Linux as well as PC/Mac
Cons: A little less user-friendliness, may provide false sense of security, has been compromised on a minority of nodes, without more advanced configuration some observers will be able to tell you’re using Tor (but not anything more, such as who or where you are)
Download: Tor Project website
Does using one of these browsers make you safe online?
Not necessarily. There are many other ways you could be vulnerable. For instance, a good browser probably won’t save you from bad browsing habits. Browsers also don’t affect the data you send and receive via apps and programs. A key online precaution to take in addition to using things like Tor or Epic is to use a VPN. Keep an eye on our privacy section for more tips to stay safe online.
Featured image by g4ll4is (Flickr).
COMMENTS
Search
Related Posts
Recent Posts
- Make Prism.js show line numbers by default (without CSS classes)
- Hemingway App 3.0 update review: A gimmick becomes a real app
- Hugo vs. WordPress page load speed comparison: Hugo leaves WordPress in its dust
- Hemingway App 2.0 update: A worthwhile update comes with unfortunate price hike
- How to view academic journal articles off campus using your library's proxy
categories
Support This Site
Bitcoin Donations:18DP9TGdPN5usTKMRMfPk6Q2mSr4mAz8NJLitecoin Donations:
LPKQbDPykwjXr5NbXfVVQH9TqM5C497A16